
I’ve been a big fan and investor of Telegram and its ambitious TON coin project from the start. Telegram’s seamless communication features combined with the innovative blockchain technology behind TON coin made it a compelling venture. However, as the infrastructure is still relatively new and lacks robust support, users are exposed to significant risks, including scams and threats.
Despite its popularity, Telegram doesn’t offer the protection to safeguard your investments from cybercriminals. Unfortunately, I learned this the hard way. My friends at AMLBot, a service dedicated to tracking stolen cryptocurrency, have been instrumental in helping people in similar situations. They work tirelessly to recover lost assets, but the challenge remains daunting.
In this article, I will share my personal experience with Telegram and TON coin, outline essential steps to protect your funds, explain why Telegram falls short in providing adequate security, and discuss the grim reality of trying to recover stolen money.
Table of Contents
How TON Coin Was Stolen

Background on TON Coin and Its Popularity
TON (Telegram Open Network) coin was launched with much fanfare and quickly gained popularity due to its association with Telegram, a widely used messaging platform known for its robust security features. The promise of a decentralized blockchain platform integrated with a familiar app attracted many investors and users.
Specific Incidents of Theft
Despite the initial excitement, the security of the TON coin has been compromised in several high-profile incidents. One such incident happened to me, demonstrating the sophisticated tactics used by hackers to exploit unsuspecting users.
Methods Used by Hackers
My unfortunate experience began with a seemingly innocent request from a trusted friend’s account. He sent me a link asking for my help voting for his cousin. I was exhausted that day but didn’t think twice about following the link since it came from someone I trusted. The link led me to what appeared to be a familiar Telegram interface, complete with a request for a one-time password (OTP) and my Telegram password.
The interface was so convincing that it even provided tips for the password, further solidifying my belief that I was interacting with the legitimate Telegram ecosystem. However, my wallet was emptied within seven minutes of entering my details, and my Telegram account was permanently deleted. The sophisticated nature of this phishing attack left me with no chance of recovering my funds or account.
This incident highlights the pressing need for heightened security awareness and the implementation of protective measures when dealing with cryptocurrencies like TON coin. In the next sections, I will share insights on protecting your funds and why recovering stolen money from Telegram is nearly impossible.
How to Return Stolen Crypto

After you realize your crypto was stolen, acting is highly important. You shouldn’t wait until scammers withdraw money from the blockchain or use mixers to confuse the investigation. Here are some steps that will help you to return stolen crypto.
Immediate Steps to Take After Theft
- Database Research: The first crucial step after discovering your crypto has been stolen is to conduct thorough research to trace your funds. Utilize blockchain explorers and other tools to identify where your money has been transferred.
- Contact Exchanges: Once you have pinpointed the location of your funds, contact the relevant cryptocurrency exchanges immediately. Provide them with the transaction details and request that they freeze the assets. Prompt action is critical to prevent further movement of the stolen funds.
- Risk Checkers: Be cautious when receiving cryptocurrency; accepting stolen funds can block your assets. Use risk-checking tools to verify the legitimacy of any funds you receive to avoid complications.
Legal Avenues and Law Enforcement
After identifying the stolen funds and contacting the exchanges, you may need to take additional steps depending on your location:
- Exchange Request: In addition to freezing the funds, you can formally request that the exchange hold the assets until further investigation. Some exchanges have protocols for handling stolen funds and may assist in recovering them.
- Report to Police: Depending on your jurisdiction, filing a report with local law enforcement may be necessary. Provide them with all relevant information, including transaction IDs, exchange communications, and other pertinent data.
Success Stories of Recovered Funds
While recovering stolen cryptocurrency is challenging, there have been successful cases. While at AMLBot, I witnessed firsthand the power of coordinated efforts in fund recovery. In one instance, our team traced and returned stolen funds within a week, showcasing that swift and strategic actions make recovery possible.
Following these steps can maximize your chances of recovering your stolen cryptocurrency. However, prevention remains the best approach, which I will discuss in the following sections: protecting your assets and understanding the limitations of Telegram’s security.
Vulnerabilities of Telegram

As mentioned, I was a big fan of Telegram and TON coin. They have a solid business model and a significant background in real business, so my investment had an enthusiastic background. In previous articles, I told how to make money on the TON project and how to earn passive income in the TON wallet. But after the scam, I have faced vulnerabilities that weaken your funds in the face of threads.
Lack of Immediate Support in Telegram
You can find official Telegram support here: https://telegram.org/support
One of Telegram’s most significant vulnerabilities is the absence of timely support. When dealing with cryptocurrency, time is of the essence, and delays can be costly. Unfortunately, Telegram’s support is notoriously slow. Volunteers might ask you to wait up to two weeks for a response, which is far too long when dealing with stolen crypto. In the meantime, scammers can easily use mixers to obfuscate the transaction trail or withdraw funds, making recovery nearly impossible.
As one of my friend told once: Telegram have no support, they have like 30 people in staff. Decentralized applications have their plus as they are open source, and it is very wise to let anyone fix bags and receive internal currency – like in an ideal world. They are so good at making business economy decisions, but they provoke vulnerability. It will take a long time to receive the answer. I hope in the future, there will be a chance for profitable protection to hire a support team.
Opaque Transaction Records in TON blockchain
In any blockchain, you can track your wallet income and its outcomes. That is the primary benefit of blockchain and the main principle of work.
You can scan your TON and NOT wallet just here: https://tonscan.org/
So, if you have been scammed or your TON was stolen, you can track where your money is. For a deeper understanding, let’s consider how the TON blockchain works.
How TON Blockchain Works
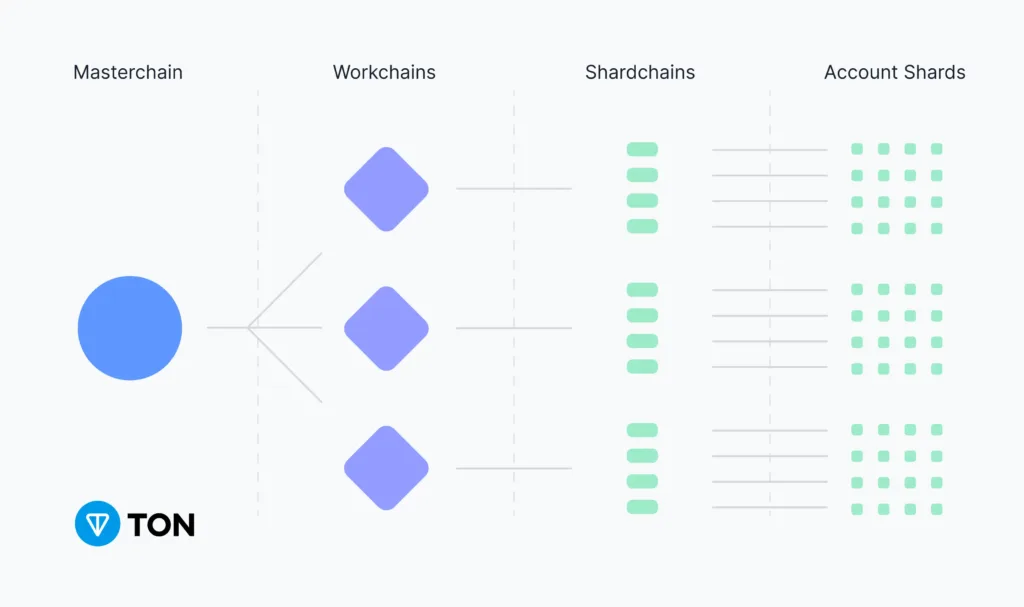
The TON Blockchain is designed to be a “superserver” capable of handling millions of transactions per second. It is built to support fast and secure decentralized applications, including DeFi (Decentralized Finance) and DAOs (Decentralized Autonomous Organizations).
Key Features:
- Sharding for Scalability:
- TON uses sharding to divide the network into smaller parts, or “shards.” Each shard processes transactions independently, allowing the network to handle many transactions simultaneously without slowing down.
- Proof of Stake (PoS) Mechanism:
- TON employs a Proof of Stake consensus mechanism, where validators are chosen to create new blocks and confirm transactions based on the number of tokens they hold and are willing to “stake” as collateral. This system ensures secure and energy-efficient transactions, as it doesn’t rely on energy-intensive mining processes like Proof of Work.
In summary, TON Blockchain’s design, featuring sharding and a PoS mechanism, efficiently supports a high volume of fast and secure transactions, making it ideal for advanced decentralized applications.
Main Vulnerability of TON blockchain
Another critical vulnerability lies in the transparency of transaction records within the TON blockchain, especially when using Telegram messages to send crypto. While the convenience of sending money through a simple Telegram private message is appealing, it also introduces significant risks. When you send crypto through Telegram, it goes to a standard wallet, and the transaction details become obscured.
So, when you use this amazing thing, like sending TON, NOT, or USDT via Telegram Messages, your funds go to the common TON wallet, and records are not reflected on the TON blockchain.
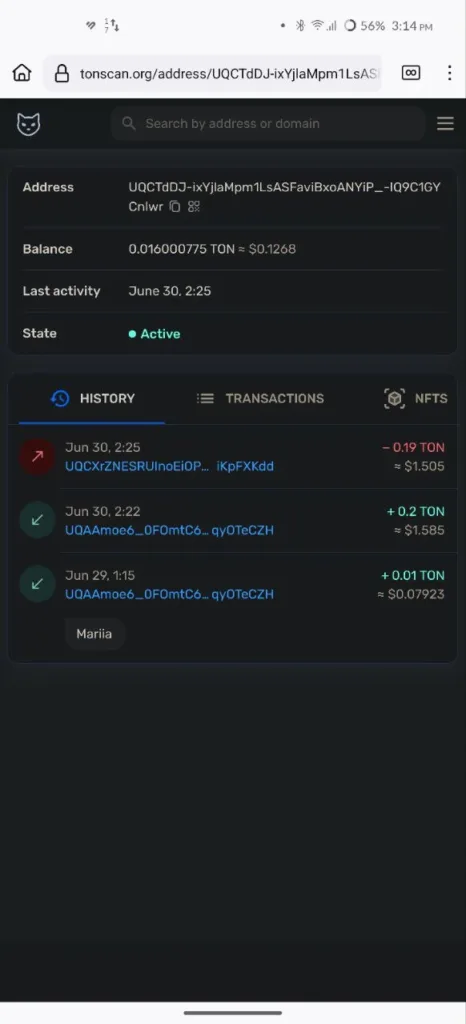
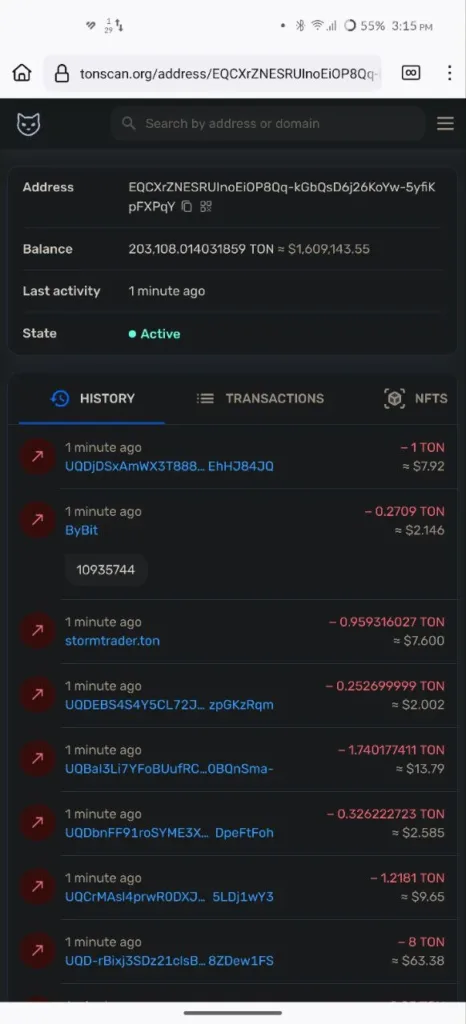
This lack of transparency makes tracking where your money has been sent challenging. This setup is perfect for scammers, as it makes it exceedingly difficult for victims to trace and recover their stolen funds.
Risks Associated with TON Coin

Common Security Risks with Cryptocurrencies
Cryptocurrencies, including TON Coin, are vulnerable to several common security risks:
- Phishing and Scams: Users may fall victim to phishing attacks, in which malicious actors impersonate legitimate entities to steal private keys or passwords.
- Hackers and Malware: Cybercriminals use hacking or malware to steal funds from cryptocurrency exchanges and wallets.
- Volatility and Market Risks: Cryptocurrency prices can fluctuate dramatically, leading to potential financial losses.
Specific Risks Of TON Coin
TON Coin faces unique risks due to its integration with Telegram:
- Limited Support: Telegram lacks robust customer support, which can delay the resolution of issues related to TON Coin transactions or security breaches.
- Opaque Transactions: Sending TON coins through Telegram messages obscures transaction details, making it challenging to track and recover funds in case of theft.
Comparing Risks with Other Cryptocurrencies
Compared to other cryptocurrencies, TON Coin’s risks are exacerbated by its reliance on Telegram:
- Integration Risks: TON Coin’s integration with Telegram’s messaging platform introduces additional vulnerabilities that are not present in standalone cryptocurrencies.
- Regulatory Uncertainty: Different jurisdictions may regulate TON Coin differently, posing legal risks to users and investors.
Preventative Measures
Best Practices for Secure Cryptocurrency Use
To enhance security when dealing with TON Coin and other cryptocurrencies, follow these best practices:
- Use AMLBot for Monitoring: Regularly monitor transactions with tools like AMLBot to detect suspicious activity and potential theft.
- Cold Wallets: Store cryptocurrencies offline, using cold wallets to minimize the risk of online hacking.
- Secure Passwords and 2FA: To protect accounts from unauthorized access, implement solid and unique passwords and enable two-factor authentication (2FA).
Enhancing Telegram Security
Improve security when using Telegram for cryptocurrency transactions:
- Two-Factor Authentication (2FA): Enable 2FA to add an extra layer of security to your Telegram account.
- Education and Awareness: Educate yourself and others about common scams and phishing tactics to avoid falling victim.
Tools and Services for Added Protection
Explore additional tools and services designed to enhance cryptocurrency security:
- Hardware Wallets: Consider using hardware wallets to secure the storage of cryptocurrencies.
- Security Audits: Conduct regular security audits of cryptocurrency platforms and wallets to identify and address vulnerabilities.
By adopting these preventative measures, users can mitigate risks associated with TON Coin and other cryptocurrencies, ensuring safer transactions and asset protection.
Conclusion
The journey with Telegram and TON Coin has been both exciting and challenging. As an early investor and enthusiast, I’ve witnessed firsthand the potential of integrating blockchain technology with a popular messaging platform. However, this journey has also highlighted critical vulnerabilities and risks that users must navigate.
While innovative, Telegram’s infrastructure lacks the robust support necessary to safeguard investments adequately. Delays in customer support can be detrimental, especially in the fast-paced world of cryptocurrency, where every moment counts. My experience with a phishing attack underscored how quickly funds can be lost and how challenging recovery can be, even with tools like AMLBot.
The risks associated with TON Coin, such as opaque transaction records and limited support from Telegram, further compound these challenges. These vulnerabilities make it imperative for users to exercise extreme caution and implement stringent security measures.
Recovering stolen cryptocurrency involves a complex process of database research, contacting exchanges, and potentially engaging law enforcement, underscoring the importance of prevention over recovery. Users can significantly enhance their protection by adopting best practices like monitoring tools like AMLBot, storing funds in secure cold wallets, and implementing robust security measures like 2FA.
In conclusion, while Telegram and TON Coin offer innovative possibilities, they also demand heightened vigilance and proactive security measures from users. By staying informed, vigilant, and proactive, individuals can navigate these challenges and participate safely in the exciting world of cryptocurrency.
No responses yet